How long should your phone PIN be?
By Naomi Brockwell, Founder and Director of NBTV
Our phones are super sensitive devices. They not only contain private photos and messages, but often we have things like banking apps on them. It’s important that we keep them safe by making sure we lock them with a PIN.
But not all PINs are created equal.
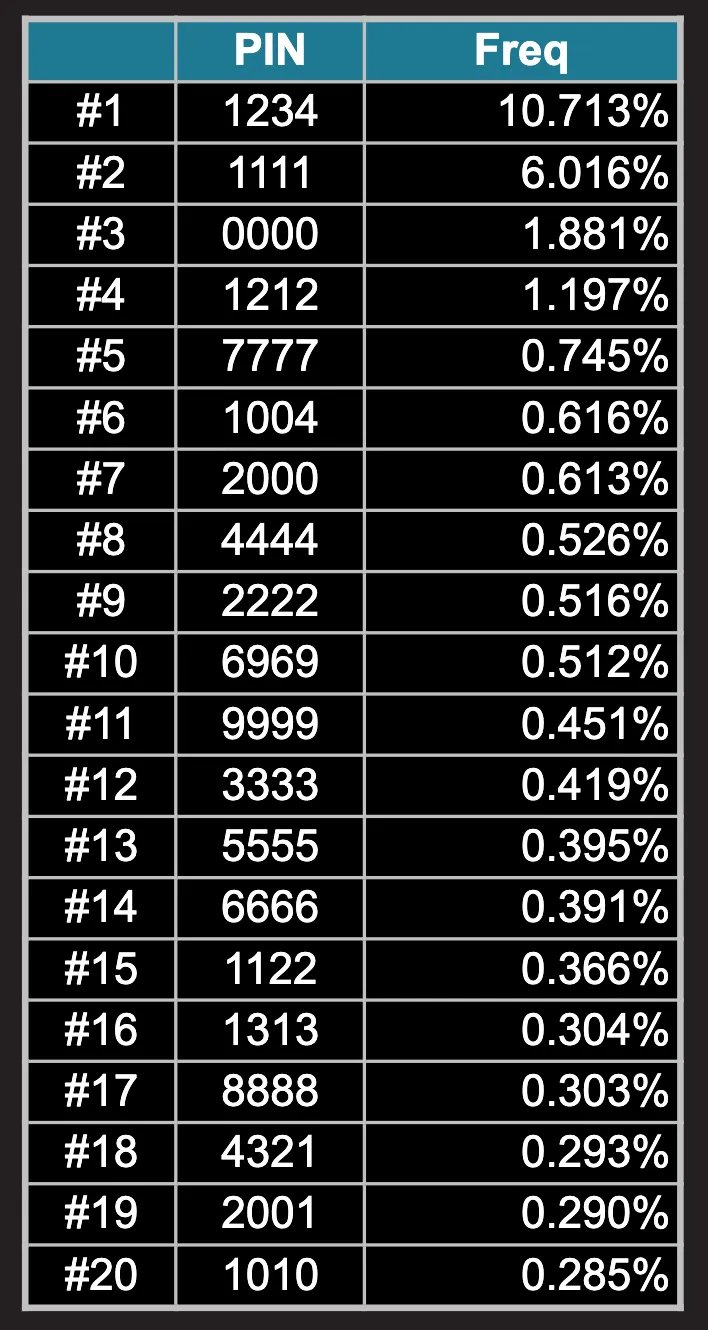
There was a study many years ago that analyzed all the PINs ever leaked in data breaches, which included millions of 4-digit passwords. It turns out that out of all the MILLIONS of leaked 4-digit passwords, 18% of people used either 1234, 1111, or 0000.
That’s not all — there were actually all kinds of common patterns that people used when choosing a PIN. Birthday formats, phone patterns, repeated numbers.
When choosing a PIN, it really should be random.
Now how long should it be?
There’s a great chart put out by Hivesystems that shows that, with modern password-cracking technology, a short PIN of 4 or 6 digits can be brute-forced instantly. This means that, generally speaking, to have robust security on your device, your PIN needs to be much longer than most people realize.
But consider this: Most people in today’s hyper-connected world will unlock their phone about 100 times a day, or around every 10 minutes or so. In theory, you might love the idea of 100% protection for your phone and using a 16-character random string of characters. And for some people, if their device is highly targeted, they might be willing to deal with a lot of inconvenience to protect it. But if you have an average threat model, having to go through this every 10 minutes will probably make you scream.
Many people will stop using privacy and security measures as soon as they become a burden. We want to find sustainable solutions for our lives, that each of us are willing to do over and over each day.
Luckily, it turns out that on some phones, your PIN doesn’t actually have to be that long in order to protect your device, because they have brute-forcing protections built into them. Pixel phones seem to have the best protections, using something called a Titan M2 chip that contains a Weaver token mechanism, and what these tools do is add a time delay to successive PIN attempts in order to prevent brute force attacks. After every wrong PIN attempt, an attacker has to wait longer and longer to try again.
This means that if you have a GrapheneOS device, or an Android that uses Pixel hardware, a random 6-digit PIN is actually sufficient for protecting your device.
Random is the key here: Remember, a user-chosen 6-digit PIN will be easier to crack.
There are also other devices that include safeguards against brute-force attacks, such as modern iPhones, and some Samsung devices.
But the delay functionality found across many of these other devices is easier to bypass than the protections found on a Pixel phone.
According to recent documents from the digital forensics company Cellebrite (a company that extracts data from mobile devices for law enforcement and intelligence agencies), Pixel 6 and later, and the latest iPhones, are the only devices where a random 6-digit PIN can't be brute forced in practice. It’s yet another reason to love GrapheneOS phones, providing robust security with just a 6-digit PIN.
For example, Samsung's brute force protections are apparently a lot weaker than modern Pixels and iPhones, and just recently Cellebrite was able to crack a high-profile Samsung phone for the FBI in 40 minutes.
404 Media has published these leaked documents if you want to get an idea of how secure your device is. Be aware that these brute-force attacks are going to require a certain skill level to pull off, which means they’re likely to be more targeted attacks and not in everyone’s threat model.
Balancing security and convenience is crucial for protecting our sensitive information on mobile devices. While strong, random PINs are essential, we have to make sure they’re sustainable. Choosing devices with advanced brute-force protections, like those found in Pixel phones, can offer robust security without compromising usability. Leveraging these technologies ensures your data remains secure against sophisticated attacks, providing peace of mind in your everyday digital interactions.
A version of this article first appeared in video form on NBTV. NBTV is a non-profit educational platform that teaches people how to reclaim control of their lives in the digital age. They give people the tools they need to take back their privacy, money, and free online expression.
Learn more at NBTV.media